This is very useful
Posts made by Shaavi
-
මොනවද මේ JWT කියන්නෙ ?posted in Blogs
“JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.”
When to use JWT?
-
Authorization: This is the most common use of jwt. Everytime a user is logged in to the system, a token is generated to the subsequent user. This permits the user to have access to use the routes, services, and resources whenever he needs.
-
Information Exchange: JWts are a great way of securely transmitting data between two parties. As the jwts can be signed, for example using public/private keys of each user it is possible to identify whether the senders are people who they say they are. As the signature is calculated using header and a payload it is possible to verify that the content hasn't been tampered with.
What is the JWT structure?
JWT consist of three parts separated by dots (.), which are:
- Header
- Payload
- Signature
Therefore, a JWT typically looks like the following.
header.payload.signatureHeader
Headers consist of type of token which is JWT, and the hashing algorithm such as HS256, HMAC, SHA256 or RSA.
{ "alg": "HS256", "typ": "JWT" }Then, the above JSON is Base64Url encoded to form the first part of the JWT.
Payload
Payload contains claims which are the information about the entity
The JWT specification defines seven claims that can be included in a token. The registered name claims are:
- iss
- sub
- aud
- exp
- nbf
- iat
- Jti
You can also use private name claims which is used to convey identity related info such as name or category. When naming these, it is necessary to avoid name collisions because public and private claims are not registered.
An example of payload could be:
{ "sub": "1234567890", "name": "John Doe", "admin": true }The payload is then Base64Url encoded to form the second part of the JSON Web Token.
Signature
This is made using the encoded headeer, encoded payload, secret, the algorithm specified in the header, and sign.
The below signature is created using the HMAC SHA256 algorithm.
HMACSHA256( base64UrlEncode(header) + "." + base64UrlEncode(payload), secret)You can use https://jwt.io/ whenever you want to check jwt tokens and see the connection between the header, payload, and the signature.
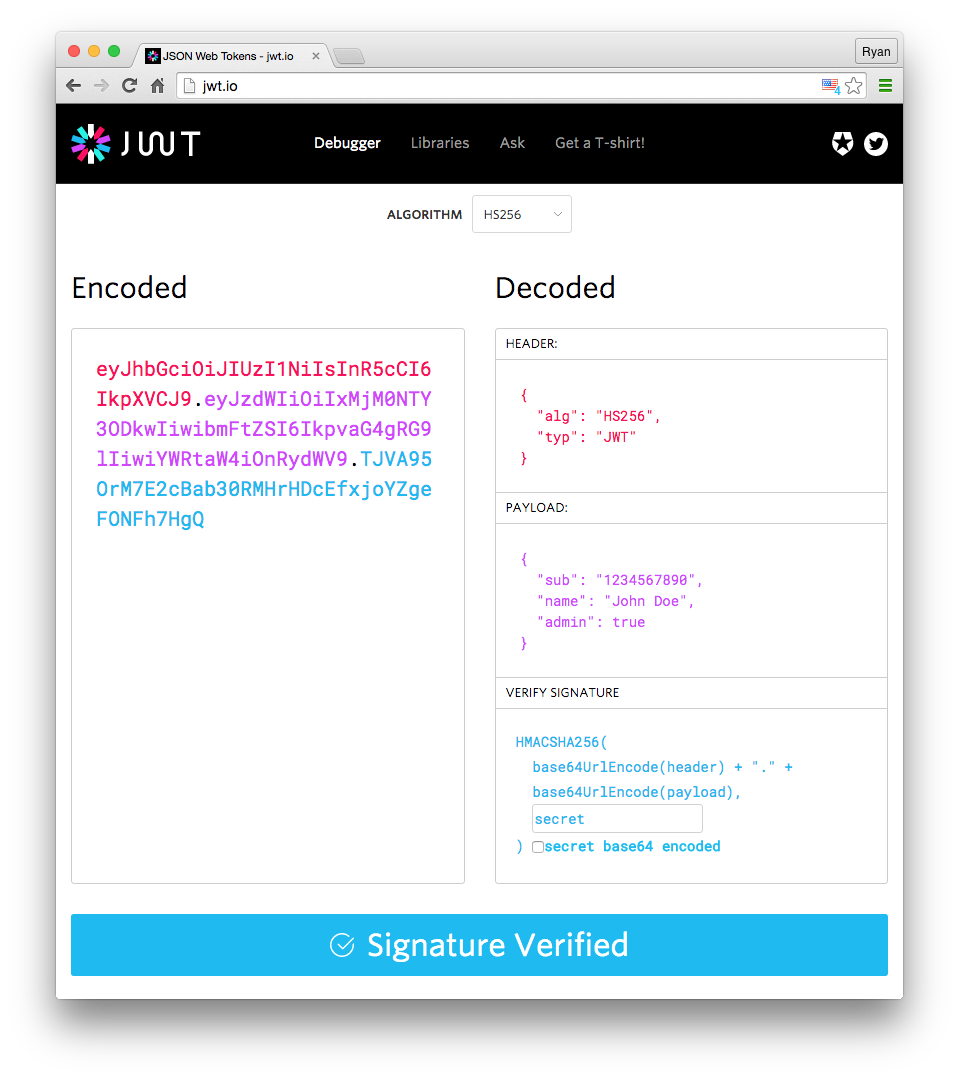
-
-
Theory Behind Blockchainposted in Blogs
You may have heard of the term blockchain, bitcoins and cryptocurrencies earlier. But what exactly are those. Blockchain is the technology behind almost all the digital currencies in the world. So without blockchain bitcoins and cryptocurrencies will not exist.
According to Don & Alex Tapscott blockchain can be referred to as, an incorruptible digital ledger of economic transactions that can be programmed to record not just financial transactions but virtually everything of value. In simple blockchain is a public ledger which records anything of value.
Basic Terminology
Record : Any kind of transaction or a deal
Block : A bundle of records
Chain : A set of blocks
Node : Computers in the networkFor example, let's consider a transaction where a deal gets included in a blockchain in which one party sells two coins for $100.
-
Step 1 : A record is created regarding the trade. The record consists details about the trade including digital signatures from each party.
-
Step 2 : The record is checked by the computers in the network called “nodes” in order to make sure the transaction is valid.
-
Step 3 : The record is then added to a block. The blocks contain a unique hash for each block with the hash of the previous block.
-
Step 4 : Each of the blocks are added to the blockchain where each blocks are connected together with the unique hash codes.
What if hash is changed?
As the blocks are connected using a unique hash of every block, a block contain the hash of the previous block too. So when changing a hash of a block, the hash of the next block should also be changed accordingly and so on. Recalculating hash of all the blocks need a huge computing power so it is considered that changing a hash is impossible.
There are some key advantages in using blockchain for various needs.
-
Trust and Transparency : One of the main reasons to use blockchain is trust and transparency. As this is a public ledger every person can see what is happening in the blockchain.
-
Cost Effective : As blockchain is a peer-to-peer network where any person can work directly there is no need for a central third party to work on behalf of someone.
-
Unbreakable : Blockchain are unbreakable as the blocks are connected with a unique hash. Once a transaction is completed and added to the blockchain they are protected by cryptography.
-
Availability : Due to the positivity of blockchain being a peer-to-peer network and a public ledger it is available for everyone.
-
Decentralized : This is the most important and core advantage of blockchain. It can be said that all the other advantages exist due to this key feature in blockchain.
-
-
Challenges of Big Data Analysisposted in Blogs

Due to the technological advancements of the 21st century data is getting advanced day by day. Data size is not calculated simply in gigabytes or terabytes, but it is also calculated in petabytes, exabytes and zettabytes.
Big data can be further identified by its characteristics, which is simply known as the 3Vs, which stand for Volume, Velocity and Variety.
The volume considers the large quantities of data found in big data as the name implies. Velocity refers to the rate in which data can be processed and retrieved when needed. It considers how fast data can be generated, stored and gained. Variety refers to different types of data. Data gained from different sources such as sensor data, data from smartphones, social media data provide different types of data.
Big data faces different types of problems during its data cycle.
Heterogeneity and Incompleteness
It is a fact that natural information consisting different types of data has more depth than structured homogeneous data. Analyzing unstructured data is problematic. It takes more time and money rather than analyzing structured data. So as a first step in data analyzing, data must be structured carefully. Greater structure is likely to be needed by most of the computer programs to work in the modern world although heterogeneous data is more valuable. However, for efficient representation, analyzing and interpretation of semi structured data requires further work.
Timeliness
When the size of the data set is getting increased the speed of having processed data is decreased gradually. It’s a challenging task to obtain processed data when there are so
much data to be checked. However when it comes to the velocity of big data analysis it not only says about the size of the data set but it also refers to the acquisition rate challenge too.Scale and Complexity
Managing large and rapidly increasing data has become the main challenge when handling big data. But now the challenge of this has become insolvable as the data volume is scaling faster than computer resources. The other move is that cloud computing has become a trending method to store big data. Cloud computing enables to work and store data and to return the required data in a fixed amount of time.When the data sets are getting bigger everyday, data storage methods and techniques should be found accordingly. In cloud computing, after a certain amount of storage limit is reached, high maintenance costs are common to access more storage space. Because of this, the scale and complexity of big data has become a major challenge in handling these.
Privacy and Security
Big data increases the sources for different data sets. However it is problematic to ensure whether these data can be trusted or not. The trustworthiness of the data set should be verified and technologies should be introduced in order to identify maliciously inserted data. The security violation of big data can happen in many ways such as data modification and manipulation, unauthorized release of information and denial of resources. Sometimes when there is less security, unauthorized users may try to attack and access files which are confidential. Security of big data can be ensured using authorization, validations, encryption and audit trails. Although there are steps taken to manage security aspects unauthorized users may get in to the systems and attack the systems which is now considered as a major challenge in big data analytics.
Most common challenges we recognize from data acquisition to result interpretation occurs due to the above reasons. So that before it gets late to get the value of big data new methods should be introduced to mitigate these challenges.
-
Tips and Tricks in debuggingposted in Blogs
Every developer goes through a stage of debugging. But at times the time taken to debug the product is greater than the time taken to develop the product. Following the below steps in debugging can save your valuable time.

Reproduce bug before changing code
In many cases, developers read the description of the bug, make random assumptions of the bug and start changing the code. After all, even though the developers think it is done, the bug has not been fixed and instead has created more bugs in the system. In order to avoid wasting time in needless bug fixes and code changes, it is better to reproduce the steps and make sure how the bug occurs. Writing some test cases to identify the bug can also be done in this situation.
Understand stack traces
The ability to understand stack traces can save hours of your precious time. The root-cause which leads to the bug can be wrapped inside a couple of layers. So understanding and managing to go through stack traces will be a great way to follow the error code. Other than that, inspecting the console and the network is a commonly used way to identify the main cause of your bug.
Know error codes
HTTP error codes are fundamental in almost all the types of apps these days. So, knowing the meaning and having an experience in the error codes can be a great way to identify where you have gone wrong. These types of errors can be occur in database drivers and protocols as well. If you ever see an error code, best thing is to Google it go through the docs on the way to get rid of the error. Below are a few examples of error codes and the cause of the errors.
· 404 - You might have the wrong URL in your app
· 401 - Your credentials are likely wrong
· 429 - You’re making too many requestsUsing git bisect
Git now provide services not only for version control, but it has few commands to help you debug your source code projects. git bisect can help you search your Git commit history to determine when a bug was introduced. This is more efficient when you have a clean commit history and it is done through binary searching commits and asking you to verify whether or not the bug exists in each commit.
Get help from social sites
In some cases, people are not able to fix the bug at the end of the day. That is the time for you to get the help from social platforms or communities. These problems can be issues with libraries, integrating tools or from an external dependency. Issue reviews in most open source projects in GitHub give a clear idea of the project issues. Finding the problems in these issue reviews can be great help when identifying the cause of the error. In addition, stack overflow serves as a platform for users to ask and answer questions via active participation, to vote questions, answers up or down, and edit questions and answers.
The strategies in debugging can vary from one person to another. So identifying the best way to efficient debugging can make you save your valuable time.So, in order to understand what suits you the best, start coding.
-
Agile methodology in software developmentposted in Blogs
The meaning of the word Agile is the ability to adapt and react in a quick and efficient way to the changes in the environment and demands imposed by the environment. It is a term for iterative and incremental software development method. Every time we need a solution which is more visible for customers and a solution which is more responsive for changes without compromising the quality of the solution we should use Agile methodologies.
The characteristics in Agile are, modularity, iteration, incrementation, adaptive, collaboration, and being people oriented. There are different types of agile methodologies which are used.
Scrum
Scrum concentrates mostly on how to manage tasks within a team based development environment. There are three main users, the scrum master, product owner, and the development team. The scrum master is the head of the development team and he is the person who holds daily standup meetings so that the development team get a chance to clear the obstacles on their development path. The product owner is the person who is in need of the system and he or she prepares the product backlog with all the requirements of the system. The development team carries out the obligation to develop the product on time.
Lean
Lean methodology is based on the principle of “just in time” (JIT) production. Eliminating waste can be seen as an important characteristic in lean because time, money, and other resources are saved because we do not continue working with unnecessary development. The product owner can decide the requirements as late as possible and the developers can deliver as fast as possible.
Kanban
In kanban the development team should visualise what they are going to do today. They must consider the workflow of the requirements and features and should choose the most important feature that needs to be developed.The amount of work in progress is limited here because every time a requirement is done the developers always choose the next most important feature to complete so that the flow is enhanced.
Extreme programming
This is useful when there are constantly changing demands and requirements from the customers. This should promote high customer involvement and rapid feedback loops for successful development. Main aim of extreme programming is to deliver high quality software quickly and continuously. So that releases take place every 1-3 weeks with continuous testing and continuous planning.
Dynamic systems development method (DSDM)
DSDM provides an agile project delivery framework for rapid software delivery. Key principles of this is business needs, active user involvement, empowered teams, frequent delivery, integrated testing and stakeholder coordination. DSDM focuses on the useful 80% of the system which can be obtained by the critical 20% of development. Projects are prioritised using MoSCoW rules where M stands for Must Do, S stands for should do, C stand for could do and W for won’t do.
It is seen that there are many different Agile methodologies that are available. But not all can be used in order to get the maximum benefit of the software development plans. The principles and values of the organisation, the realities of the product you are going to be developing, and the status of the stakeholders must be understood by companies and other individuals in order to make their products successful.
-
RE: Share your knowledge and experience and win a t-shirtposted in Announcements
Why cant I submit posts? It syas "Not enough tags. Topics must have at least 1 tag(s)"